SOLIDWORKS PDM & Windows Active Directory: A Master List
While this guide contains a lot of great information about basic setup topics, “do’s and don’ts”, and troubleshooting, many of the configurations and steps are what we’d consider a more “advanced” topic, and should only be taken by or under the direct supervision of a SOLIDWORKS PDM Admin or IT Administrator. Please reach out to Technical Support if you’re unsure or have questions about any of the info found in this article.
Table of Contents
What Does Active Directory Have to Do with PDM?
Setup (And What You Should Know Beforehand)
Active Directory Sync (New with 2023 and Beyond!)
What if I Already Have Windows Users Set Up in PDM and We Switch Domains?
Common Issues & Troubleshooting
What Does Active Directory have to do with PDM?
SOLIDWORKS PDM has an inherent function that allows you to create PDM users directly in the admin tool, and those users and credentials are unique to the vault.
SOLIDWORKS PDM Professional also integrates with your Active Directory (or “AD”) listings so that Windows users can be imported into the vault, allowing users to utilize a single sign-on where their PDM credentials and Windows credentials are the same. This saves some time creating users, but also makes for a pretty convenient way to access your vault.
Setup (And What You Should Know Beforehand)
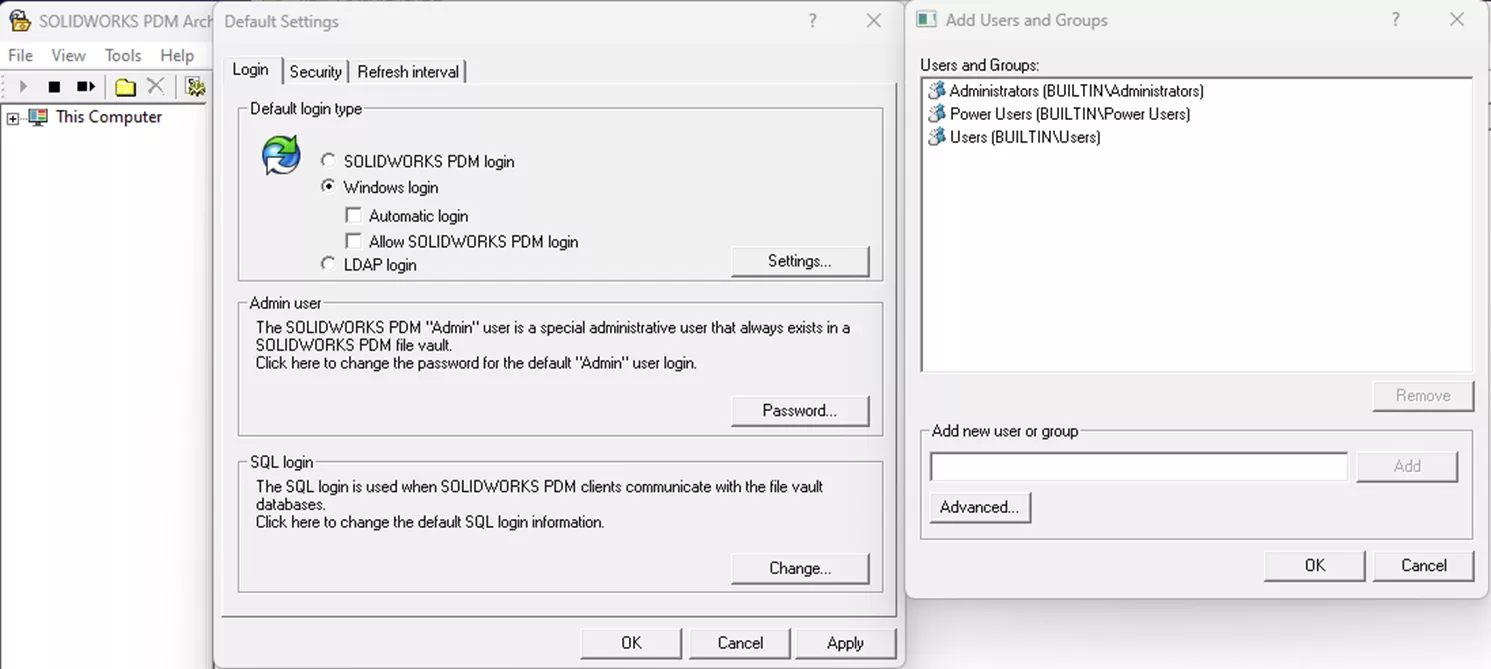
When configuring your vault for Windows users, you’ll need to first add the AD users/groups to your PDM Archive Server Configuration tool. This is what gives PDM a “pool” of available Windows users to pick from in your AD listings. Only once that’s done can you add them in the Administration tool.
See our article on adding users to your vault to read about the exact steps for adding users to the archive server, and then adding them into your actual vault.
While not explicitly related to adding users to the vault, it's important to be aware that during setup, there is something called "Attach Access" which also relates to AD.
Attach access is a permission that allows a user to create a vault view. When creating a vault view using the View Setup tool, the system will identify the currently logged-in Windows User (or the user the View Setup tool is running as, if you ran it as admin or another user) and compare it against a list of users granted attach access on the archive server.
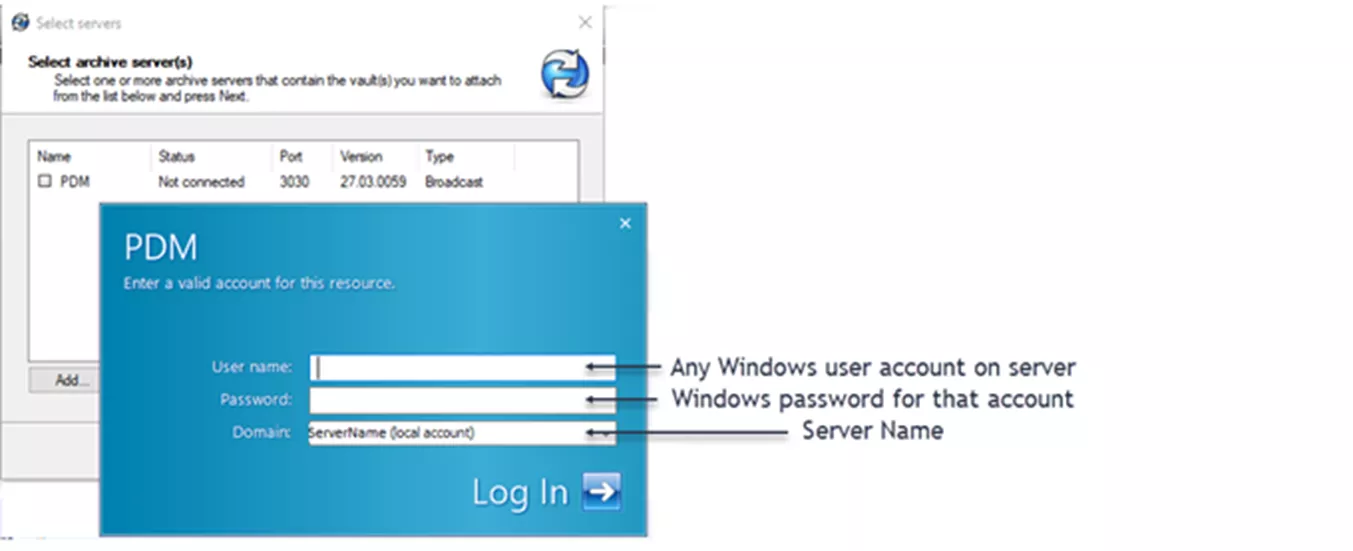
If the user doesn’t have attach access, you’ll receive a login prompt stating “Enter a valid account for this resource”, which is asking for a set of Windows credentials with attach access. While not the same as your vault users, this is just as important. You can read more about how to grant attach access here.
AD Groups in Your Archive Server Configuration
When adding AD groups to your Archive Server Configuration, it may be easiest to just add your “Domain Users” group so that all of your Windows users are there by default - but that may actually cause issues down the line.
The Domain Users group contains ALL users in your environment, and I’d guess many of those users will never even touch the vault. The larger the group(s) you add, the more users PDM has to read through and process when you try to add users in the administration tool. This can create slowdowns when adding users, or even cause timeout errors and missing users. You’re putting more strain on your PDM system, and therefore decreasing performance.
It's best practice to first create a local group on your archive server using the Edit Local Users and Groups tool.
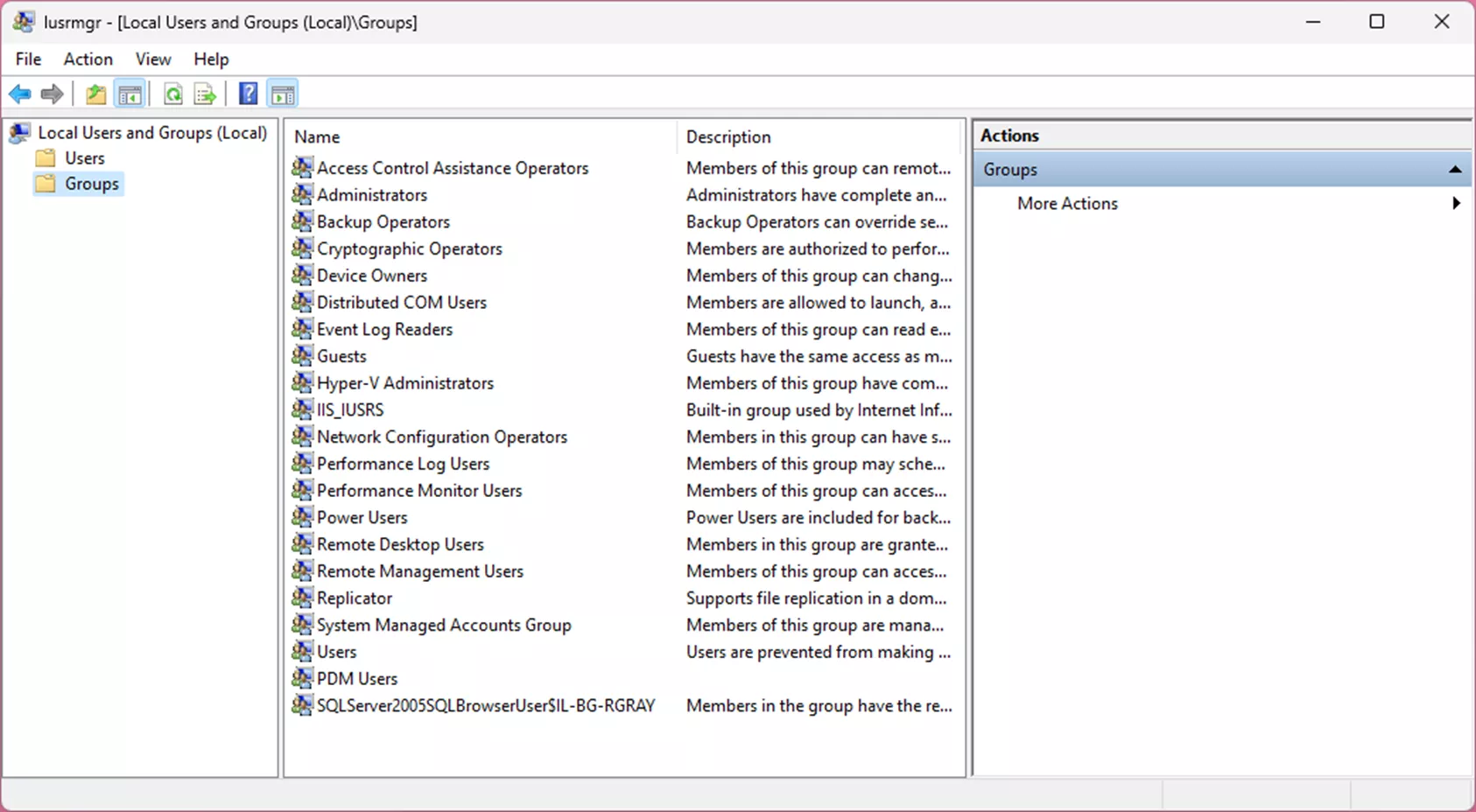
Once you’ve created the local group you can import any AD users or sub-groups (not Domain Users) into this local group.
You can then add that local group to your archive configuration. This creates the most stable setup for PDM – both in the load created by hosting only the users needed for your vault, but also in ensuring PDM only has to reach this local group for users, rather than searching the entire AD listings.
Multiple Domains & Domain Trusts
PDM can add users from domains other than the one the archive server currently resides on so long as everything is configured correctly. PDM can’t directly communicate with the external domain, so your network administrator will first need to create a trust between the two domains. The primary domain must trust the secondary domain where the users are accredited. Domain administrators on both domains must create the trusting relationship, even for a one-way trust. A two-way trust setup is the recommendation, however.
Once a trust has been established, you can then add users or groups from the other domain to the local group on the archive server that you created earlier.
Multi-factor Authentication & Smart Cards
It should be noted that SOLIDWORKS PDM doesn’t support the use of MFA or Smart Cards. There are no settings or options to allow this functionality, and it’s not something that SOLIDWORKS tests when developing the software.
Using MFA or Smart Card integrations with PDM is done at your own risk since there’s a good chance that, even if you have some success in doing so, it won’t continue to function or remain stable. Technical Support likely won’t be able to assist with any MFA or Smart Card issues that may arise.
Active Directory Sync (new with 2023 and beyond!)
In 2023, SOLIDWORKS introduced a new functionality that allows you to sync PDM users and groups with Active Directory. This allows for on-demand sync from AD into PDM, including automatically adding and removing users in PDM based on group membership in AD, removing groups in PDM that no longer exist in AD, updating user attributes from AD, etc.
Check out the What’s New in PDM 2023? to learn more!
What if I Already Have Windows Users Set Up in PDM and We Switch Domains?
If your company needs to move to a new domain and you use Windows logins in PDM, you're justified to be concerned about how this will affect your vault. The good news is that making the switch is pretty painless. There are just a few pieces of information to confirm and update depending on the new domain.
Step 1: Ensure your PDM archive server is authenticating with the correct domain controller for your new domain (this will be covered in more detail under the Network Communication subsection of Common Issues & Troubleshooting).
Step 2: Ensure the new domain users/groups are added to your archive server configuration. Or, in case of best practice, ensure the users and groups you need from the new domain are added to the dedicated local group on your archive server, and that the local group is added to your archive server configuration.
Step 3: If your Windows usernames will be different in the new domain, you’ll need to update those usernames in your vault database to match. The existing usernames in a PDM vault are matched with the login name of the Windows user (without the domain prefix) - so if user DOMAIN_1\BobS existed in the vault beforehand, the same user DOMAIN_2\BobS would be valid because the username is BobS in both places. This should match up fine so long as you updated the user groups for the new domain in the first point. If the username changes from BobS to BobSmith in the new domain, however, it will need to be updated in SQL so PDM can find it.
You can read the exact steps for updating user info in SQL here.
Common Issues & Troubleshooting
Following proper setup can help reduce a lot of problems, but there are still a few common issues we see more often than not. Thankfully, you’ll find a list of the most common issues we see pertaining to Windows logins with PDM, and the typical steps we take to resolve them.
Invalid Username and Password Error
This is an error we hear about often, and it can be frustrating when you know you’ve entered your credentials correctly. The actual error message can vary somewhat (e.g., “Invalid username or password”, “The entered username or password is incorrect”, etc.), but the general idea is that your credentials aren’t working as expected.
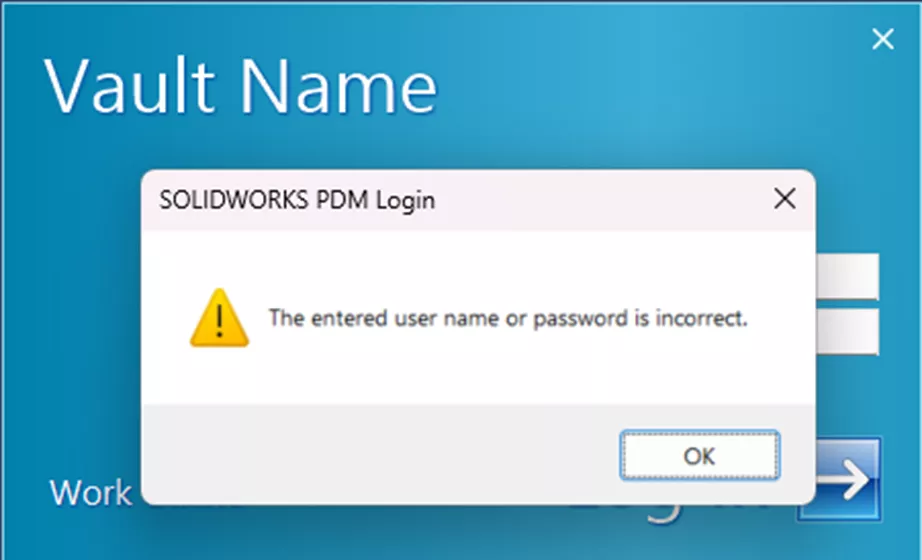
This will usually happen on only one profile at a time. There are a few common causes, including a “corrupt” profile, invalid domain configurations, and credential issues. We recommend reading our separate article for specific steps to take to troubleshoot the issue here.
Unable to Login (while receiving an error other than the error shown above)
If you’re trying to log into PDM using your Windows credentials and receive an error or behavior other than “invalid credentials”, your approach will likely be a little different.
If you’re a new user, or if your company recently made any changes pertaining to your AD or network environment, you may want to ensure your user exists in the archive server configuration tool. Your user should either be directly added to a local group on the archive server or added to a domain group that’s then added to the local group on the server. Verifying your user’s presence ensures PDM can “see” your profile and subsequently talk to your domain controller to allow you access.
Once you’ve confirmed your user exists, further troubleshooting might differ based on the error received. Let’s go over a few common errors.
“Could not access the item in the database.”
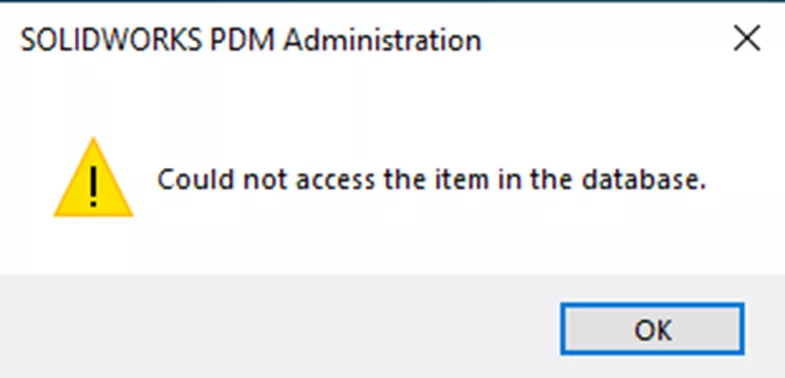
This rather vague PDM error can be triggered from multiple sources and can be difficult to diagnose properly if you're unsure what to look for. If you receive this error, obtain the PDM client log file from the machine that experienced the error, take note of what you were doing when it triggered, and reach out to support with both of those pieces of information.
“Could not connect to archive server.” / “Could not log in to the database.”
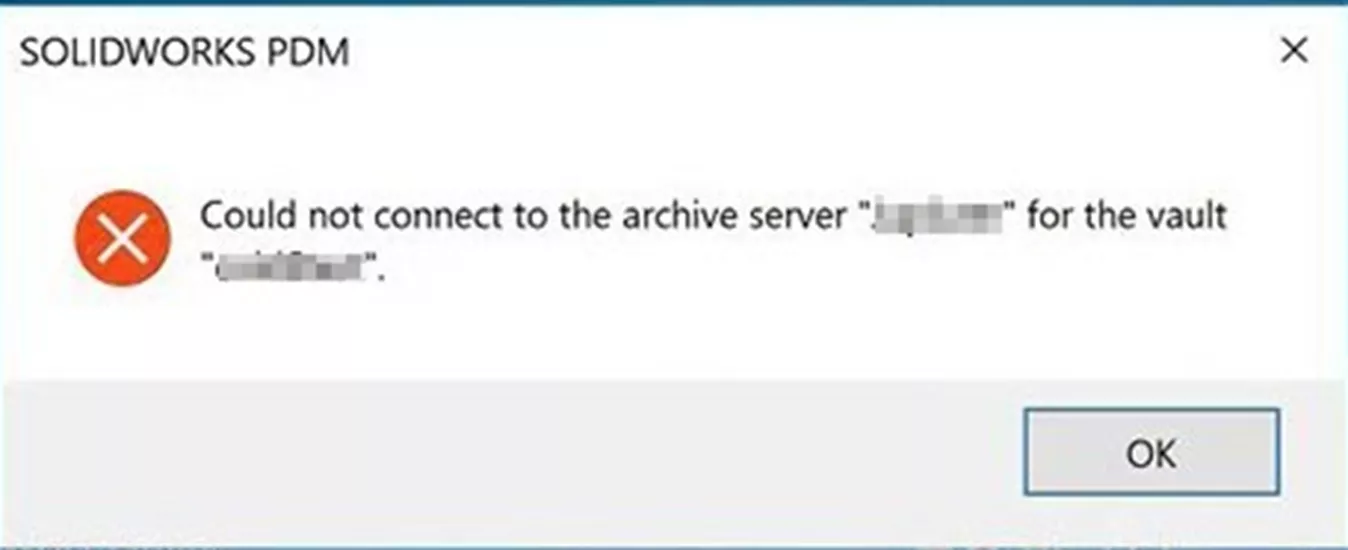
Any error pertaining to the inability to connect to your archive or database server(s) when trying to log in (not to be confused with could not access item in database) is usually network related. Check out the Network Communication Issues section below for steps on addressing this particular issue.
“Administrator has blocked your login.”
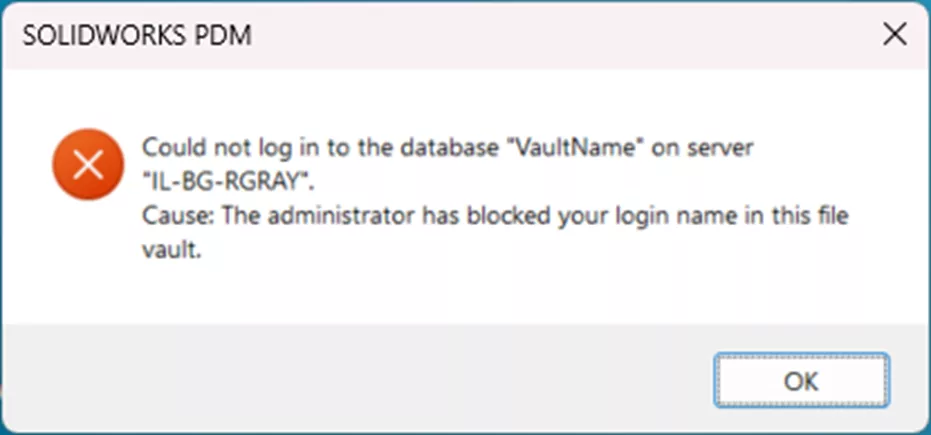
This message means your admin has checked the Refuse login administrative permission on your account in the administration tool. You’ll need to reach out to your vault admin to uncheck it and allow you back in.
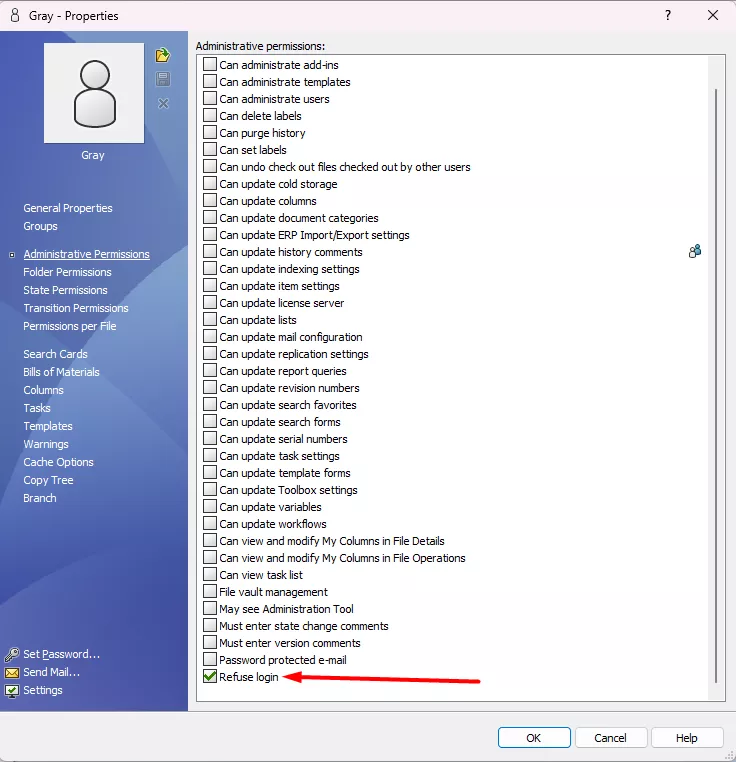
“The system is locked due to maintenance.”
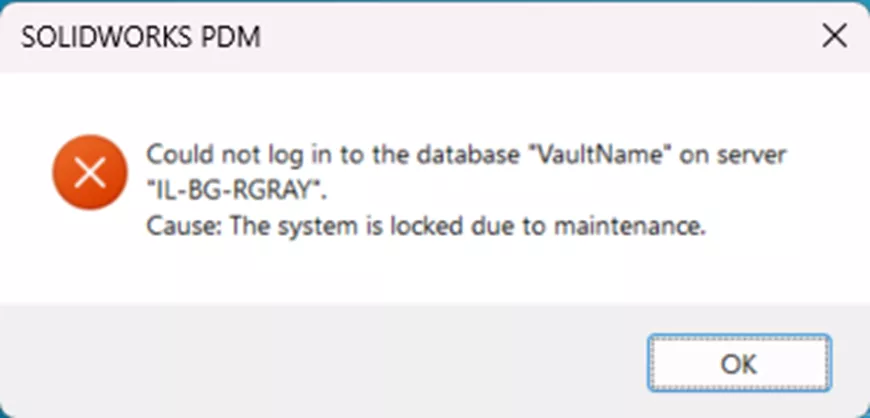
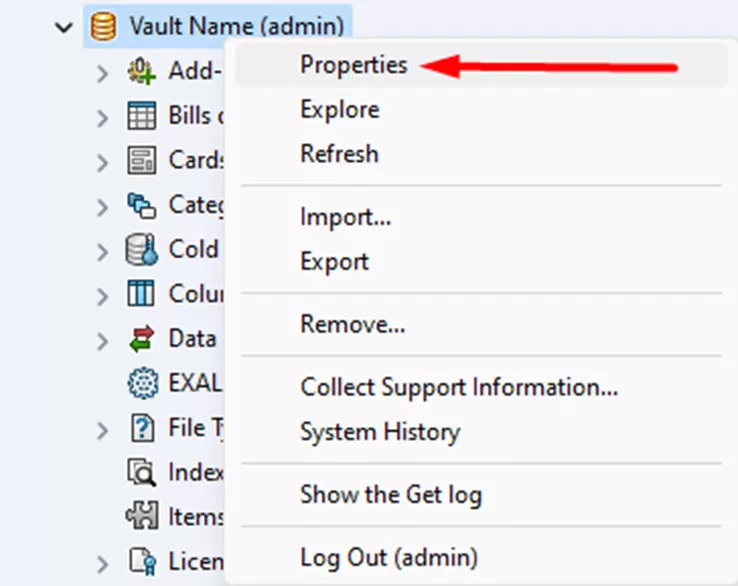
This is caused by a vault admin using the Block Logins option in the administration tool. It most often occurs during major system changes like upgrades. To turn it off, login to the administration tool as an admin and right-click the vault name > Properties.
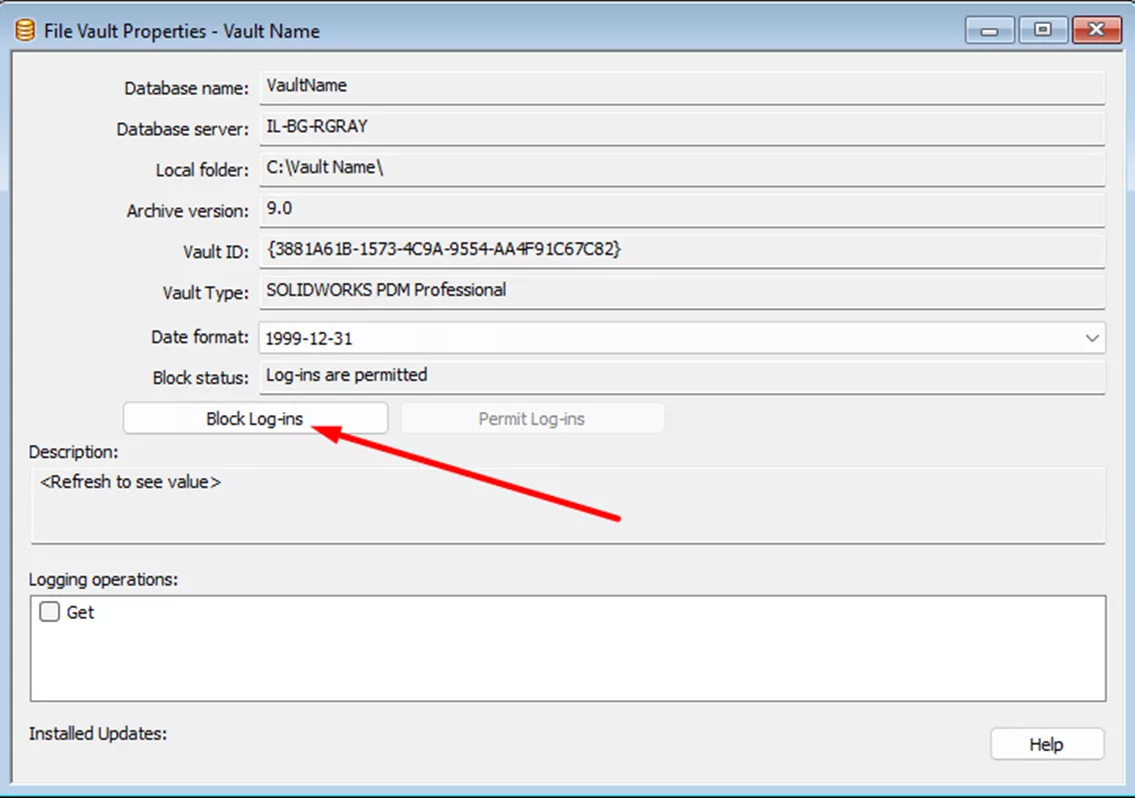
Then you can choose Permit Log-ins in the Properties screen.
Network Communication Issues
A common cause of login issues for any PDM user (not just Windows users) is network communication. Typically, these issues are with antivirus, firewall rules, or just general network routing. Start by identifying whether the basic communication methods PDM uses to talk between all its various pieces are functioning as expected.
What’s going on behind the scenes?
When you try to log in to PDM as a Windows user, the following happens:
- The client contacts the archive server with the logon request.
- The archive server then contacts the domain controller with a Kerberos v5 authentication request.
- The domain controller responds to the archive server with a success or fail for the authentication.
- The archive server sends the response to the client.
- If the response was a success, the client user logs into the vault. If it was a fail, the client user will be presented with an error.
Identifying your Domain Controller
A good basic piece of information to start with is what domain controller your archive server is authenticating with. You’ll need to know this for further troubleshooting steps, and looking to the wrong domain controller can cause a lot of issues with Windows logins for PDM. To check this, you’ll want to be logged on to the archive server.
Open up a Command Prompt by searching “cmd” in the Windows Start menu.
In the Command Prompt, type the following and hit enter: echo %logonserver%
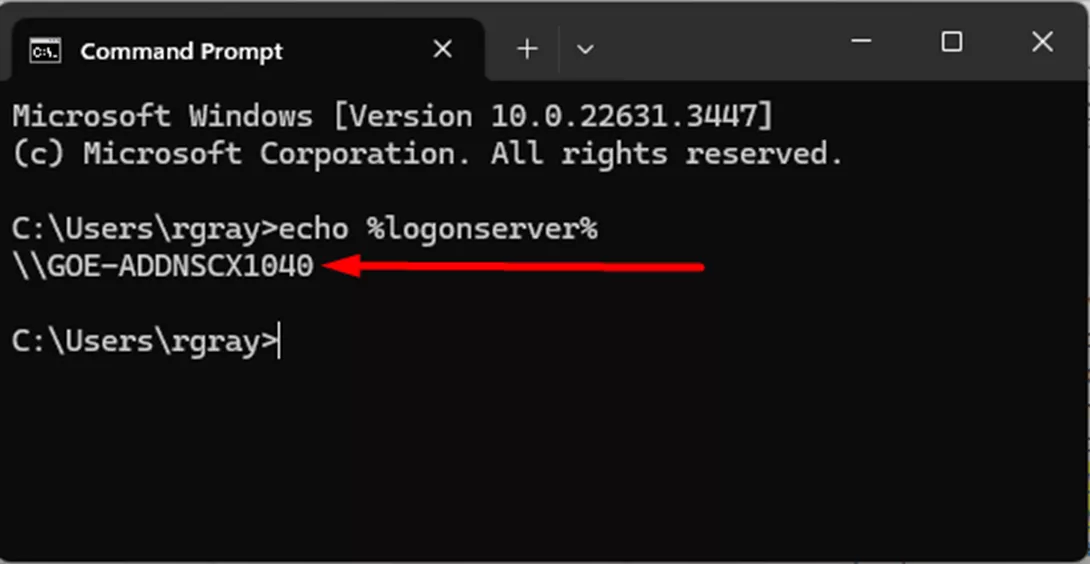
The result that displays is the domain controller the PDM archive server is communicating with.
Communication requirements and testing
There are several components on the network that PDM relies on to function properly. For Windows logins specifically, you will need to:
- Confirm the client workstation can ping the archive server.
- Confirm the client workstation can ping the local domain controller.
- Confirm the archive server can ping the client workstation.
- Confirm the archive server can ping the local domain controller.
An exception to this would be if ping is disabled in your environment. In cases like these, you’ll need to work with your internal IT to discuss confirming communication between these machines in other ways.
If you’re not sure how to perform network communication tests like ping, check out our “SOLIDWORKS PDM Network Communication Troubleshooting” article for more information on the different methods of testing, as well as communication requirements.
Related Articles
SOLIDWORKS PDM: Input Formula Aliases
Default Expressions in SOLIDWORKS PDM Data Cards
SOLIDWORKS PDM vs 3DEXPERIENCE CLOUD PDM: Workflows, Licensing & More
How to Check What Version of SQL a SOLIDWORKS PDM Environment is Running
How to Search for Variables That Have Been Left Blank in SOLIDWORKS PDM Data Cards

About Rowan Gray
Rowan Gray is a Technical Support Team Lead at GoEngineer with a specialty in SOLIDWORKS PDM and related data/lifecycle management. They have been with GoEngineer since 2020, and have a strong IT background that helps them more fully support customers with whatever issues may arise in their PDM environment. In their free time they enjoy playing video games, crocheting, and spoiling their pets.
Get our wide array of technical resources delivered right to your inbox.
Unsubscribe at any time.
